As a rule, macOS caches don’t require regular cleaning. They typically manage themselves, emptying out old files when the cache grows too large or the files grow too old. So as far as users are concerned, caches are entirely self-operating. Unless, of course, there’s a problem with the cache. And Quick Look has an interesting quirk that might cause some trouble for security-conscious users. It saves Quick Look previews of encrypted files in an unencrypted format, allowing in-the-clear viewing of otherwise encrypted files. The images are small, which reduces the impact, but only marginally. The leak is most dangerous for image content, which can be easily deciphered from even a thumbnail. It’s less threatening for text files, which typically only get icon-based previews that are hard if not impossible to read. But if you’re worried about this leak, you’ll want to take steps to contain or mitigate it as soon as possible. So here’s everything you’ve ever wanted to know about what the Quick Look cache is and what to do about this problem.
Why You Should Clear the Quick Look Cache on macOS
Quick Look is, of course, the macOS feature that provides quick previews of files from Finder. Select a file and tap the Spacebar, and a window will pop up containing a preview of the file. This is most useful for media files, but with some tweaking, it can be effective for nearly every file type. You can expand the file types previewed by Quick Look with plugins, which are available from GitHub. They might not always work, but many of them are reliably and essential. So if you rely on Quick Look, you’ll find yourself quick on the Spacebar.
When you tap the Spacebar, this generates a full-sized preview of the file. That, of course, is cached for quick retrieval later. But even if you haven’t used Quick Look to preview a file, the cache can still contain a preview image. It’s small, but it’s there and it’s definitely decipherable. As a result, a knowledgable snoop could view previews of your encrypted files without decrypting the files themselves. This is a significant security hole, and as far as we know, it’s existed for several major releases of macOS.
Quick Look’s primary service is com.apple.quicklook.ThumbnailsAgent. This service is responsible for crawling the file system and generating thumbnail-sized previews of all applicable files. Once generated, these thumbnails are cached in an SQLite database, which associates cached image files with the appropriate document. That database is stored in cleartext and can be accessed by any user. Open the database does not require superuser permissions or administrator access.
If you want to examine your own cache, you can find it on your hard drive. You’ll need to navigate to /var/folders using the “Go…” menu, since that’s typically hidden. From there, you will need to dig around a little to locate the folder named “com.apple.QuickLook.thumbnailcache” as seen below. There will be a number of randomly-named folders in between, so just explore a bit.
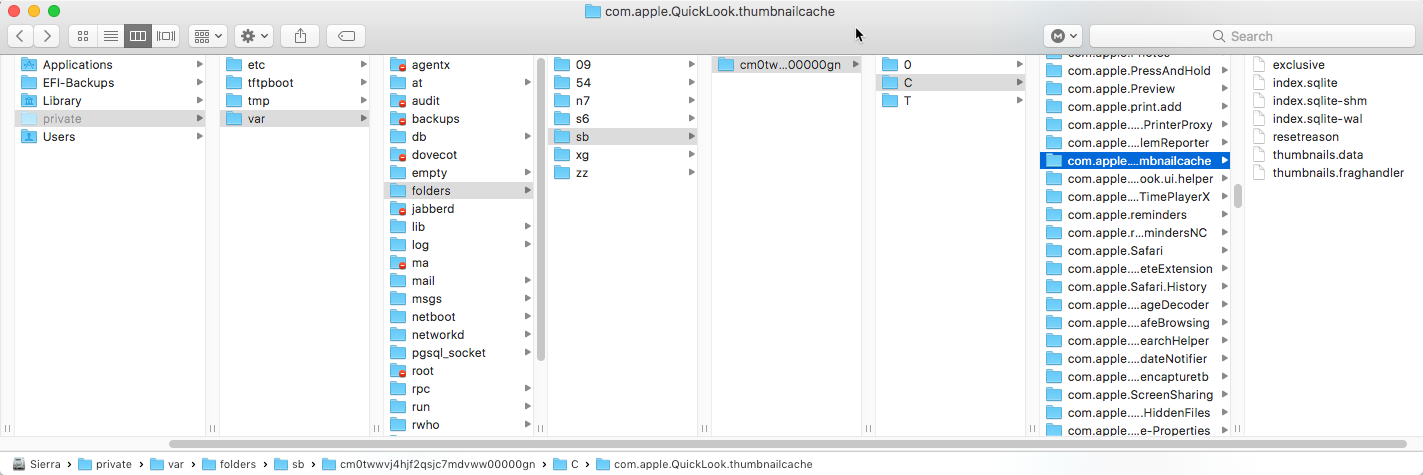
Is this a problem?
Any leaking of encrypted data is undesirable. This issue primarily a concern for images. They can reveal data even at reduced sizes. Images that have not been previewed with Quick Look will have 128 pixels on the longest side. Cached viewed images will be closer to triple that.
What about non-image files? Those get thumbnails that look like their Finder icons. Consider TXT and RTF files as an example. Those files’ Finder icons are a curled page. That’s the same thing you’d see in the Finder Preview pane. If you’re struggling to recall that icon, take a look at the cached previews below.

Notice that the RTF file has larger text. That’s because RTF thumbnails are actually responsive to the contents and styling of the document they represent. So, if you make the text in your RTF sufficiently large, it will create a legible thumbnail preview that someone could likely read.
According to the security researcher who most recently wrote about this vulnerability, thumbnails persist even after the files are deleted or their source volume is removed from the system. That means that unplugging a USB drive or trashing a file might not be as complete as you imagine. You could be leaving crumbs of your files behind in the thumbnail cache. And if you were perhaps attempting to conceal your presence on a machine, or the use of a particular USB drive, a cached thumbnail from that USB drive would be a smoking gun. In short, the preview persists after the parent file is removed.
Clearing the Quick Look Cache on macOS
Let’s solve this problem! The first step is clearing the Quick Look cache.
1. Open Terminal from “/Applications/Utilities/Terminal.app” or by typing the name of the application in Spotlight.
2. Paste the following command below into Terminal, then press the “Enter” key to execute. This will immediately stop the Quick Look service and delete cached files:
qlmanage -r cache
![]()
Disabling the Quick Look Cache on macOS
The above command will empty the Quick Look cache. This isn’t a permanent solution. Without modification, the Quick Look cache will continue to accumulate previews of encrypted and removed files.
As of now, the only way to defeat this bug is to disable the Quick Look cache entirely. It’s a blunt solution, but it works. This doesn’t disable the Quick Look functionality, just its ability to store thumbnails in the Quick Look cache. Of course, it might slow the Quick Look cache down a bit, especially for removable media. But with the speed of modern storage technology, it’s likely to be an undetectable difference.
To disable the Quick Look cache permanently, execute the Terminal command below:
qlmanage -r disablecache
If you wish to turn the Quick Look cache back on, use the enablecache command in place of disablecache.
If you’re interested in Apple devices and security, you might be interested in the following posts:





