The Internet as we know it required modern online cryptography algorithms. Without these algorithms, secure communication across the public channels of the Internet would be close to impossible. By providing an easy way to hide information from prying eyes, modern cryptography algorithms allow private communications, online banking, and digital shopping to take place all across the web, at every second of every day.
But if you have no idea how online cryptography works, you might find yourself a little confused about how it all stays so secretive. Is it just one big super password protecting your credit card information as it transmits across the tubes of the Internet? Fortunately not: there’s a complex set of cryptography algorithms working together to make sure only the appropriate parties access your sensitive information.
Symmetric Key Encryption Algorithms
Symmetric key encryption algorithms are the most basic type of encryption algorithm. They rely on a password to act as a key. If you have the password, you’ll be able to read the encrypted data. Without the password, you’ll just see a mess. Symmetric key encryption is the oldest form of encryption. It forms the basis of combination locks, simple ciphers and even modern hard drive encryption. Standards like AES, DES and Blowfish are all symmetric key algorithms. The method by which they encrypt and decrypt data is different, but each require only a password to permit access.
When you use symmetric key encryption, the safety of the password, or secret key, is paramount. If you need to share the encrypted information with another party, you’ll also need to provide the secret key. This exchange must be performed securely, to ensure that no eavesdroppers also gain access to the encrypted information. There are modern techniques like Diffie-Hellmen that allow for a key exchange over insecure lines of communication, but they required significant computational and organizational overhead to manage properly.
As a result, symmetric key encryption algorithms are almost always paired with public key encryption algorithms when used online. This allows for secure communication over open channels, but also provides the speed and efficiency of fast local symmetric key encryption algorithms.
Asymmetric Key (Public Key) Encryption Algorithms
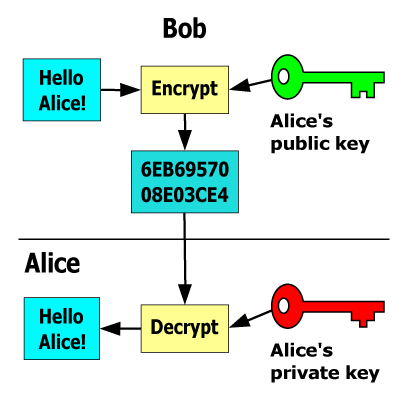
Going beyond simple symmetric key algorithms, we can use assymmetric key algorithms. The symmetrical part of symmetric keys is the password: it’s the same to both encrypt and decrypt. With asymmetric keys, that’s no longer the case. One key, called the “public” key, is used to encrypt messages. Another key, called the “private” key, is used to decrypt the messages. Each can only perform one role, and the keys are mathematically related.
Asymmetric key algorithms don’t require shared trust, which makes them ideal for secure communications between strangers. Consider the following real-world example to get a better idea of how these keys relate.
- Alice purchases a padlock and key combination. She unlocks the padlock with her key and sends the unlocked padlock to Bob, keeping the key to herself.
- Bob places his message in a box and uses Alice’s padlock to lock it. He can no longer unlock the box.
- Bob returns the locked box to Alice.
- Alice opens the box with her padlock’s key. Only she possess this key, so only she can read the message.
If Alice wants to receive many encrypted messages, she can duplicate and share her padlock widely. This way, she can receive encrypted messages and use her one padlock key to decrypt them all.
Obviously, a physical key is not an extremely secure encryption tool. It can be duplicated, or locks can be picked. The digital “keys” used in assymmetric key algorithms are numbers containing hundreds of digits, making them basically impossible to crack.
Hash Functions

What if you want to store encrypted information without revealing anything about it? You can use a hash functions. Hash functions are one-way encryption tools that convert a message of any length to a fixed-length string called a “hash” or a “digest.” Unlike other encryption algorithms, cryptographic hashes are “deterministic”: a given input always produces the same output.
This makes hash functions perfect for storing and comparing passwords. Rather than store a plaintext passwords, servers store hashes of those passwords. To test a provided password against the stored password, a hash of the provided password is compared with the stored hash. If the hashes match, the passwords must be the same. You’ll find hash functions like SHA used in storing passwords and computing digital signatures.
To ensure that this hashing proccess is secure, two messages can never produce the same hash. If they do, this is called a “hash collission.” Hashes with known collissions are not suitable for cryptographic use. Many non-secure hash functions, like MD5, were once considered secure until many collissions were found.
Security in (big) numbers
The security of cryptographic functions relies on using mathematical problems with no known efficient solutions. These problems are considered “intractable,” meaning they can’t be solved within a reasonable time span. However, many of these problems can be computed quickly in one direction, but are impossible to compute in another direction. These are called “one way” functions, and they’re perfect for cryptography.
For an example of how big these numbers are, consider the length of the numbers used in RSA-1024. According to the math, it would require 5.95 × 10^211 years to find the correct prime factors of the 1024-bit product used in RSA-1024. That’s 211 zeroes, far more than a goggol. Unfortunately, the universe has only existed for a comparatively short 13.75 x 10^19 years.
Of course, that doesn’t make RSA-1024 impossible to crack: the algorithm could have other undiscovered vulnerabilities. But brute-force evaluation of the private key will likely remain impossible without dramatic developments in mathematics and computing.
Algorithms in Use

Here are some working examples of common cryptographic methods in actual use online. You’ve likely used at least one of them today.
RSA-1024
RSA-1024 is a well-known and frequently-used asymmetric key algorithm with no known vulnerabilities. It follows the general pattern of most assymmetric key algorithms, so it provides a good example.
At the beginning of communications, the RSA algorithm generates two extremely large prime numbers. When we say large, we mean it: RSA-1024 uses 512-bit numbers, which have hundreds of decimal digits. These randomly generated prime numbers are kept secret, and represent the user’s private key.
These numbers are then multiplied together to form a product. From this product, another number is derived. That number is the public key, used to encrypt messages. That number is published widely, and can be used to encrypt a message for the owner of the private key.
The binary code of the message is combined with the binary code of the public key, and the combination forms the encrypted message. This encrypted message is sent to the user, who uses the private key (the prime factors from earlier) to undo the effect of the public key, revealing the now-decrypted message.
HTTPS (SSL/TSS)
When you see the small green lock icon in your browser’s address bar, that means a site is using HTTPS. This encrypts communications between the website and your computer, ensuring your communications stay safe. HTTPS communications are set up using a handshake, which establishes core elements of the secure communication process:
- Hello: the client and server exchange information, including SSL version and cipher suites supported. The server and client then decide on a version of SSL and cipher suite to employ.
- Certificate Exchange: the server proves its identity to the client by provided an securely-signed SSL certificate. This certificate is issued by a trusted body, called a certificate authority (CA), that has validated the identity of the server and domain. It also includes the server’s public key, used in the next step.
- Key Exchange: the client generates a random key and sends it to the server, encrypting it with the server’s public key. The server then uses its private key to decrypt the message.
Once this information is securely exchanged and identity is verified, HTTP messages can be generated in cleartext and encrypted using the shared secret key generated by the client.
Pretty Good Privacy
Pretty Good Privacy (PGP) combines symmetric key and public key encryption, similar to HTTPS. Each message in a PGP conversation is encrypted using symmetric encryption. The sender generates a random key to encrypt the message, called the session key. To allow for decryption, the session key is included with the message. To secure the message during transportation, the message and session key are then encrypted using the recipient’s public key. Only the recipient’s private key can decrypt the message and session key. Each session key is only used once.
You might also like the following posts:





